CentOS ist die dritthäufigste Distribution des Linux-Kernels. Die Abkürzung CentOS steht für „Community Enterprise Operating System“.
-
Red Hat Security Advisory 2024-4827-03
Operating System: RedHat ≈ Packet Storm Jul 25, 2024 | 13:15 pmRed Hat Security Advisory 2024-4827-03 - An update for the httpd:2.4 module is now available for Red Hat Enterprise Linux 8.6 Advanced Mission Critical Update Support, Red Hat Enterprise Linux 8.6 Update Services for SAP Solutions, and Red Hat Enterprise[…]
Read more... -
Red Hat Security Advisory 2024-4828-03
Operating System: RedHat ≈ Packet Storm Jul 25, 2024 | 13:15 pmRed Hat Security Advisory 2024-4828-03 - An update for freeradius is now available for Red Hat Enterprise Linux 9.2 Extended Update Support.
Read more... -
Red Hat Security Advisory 2024-4829-03
Operating System: RedHat ≈ Packet Storm Jul 25, 2024 | 13:15 pmRed Hat Security Advisory 2024-4829-03 - An update for the freeradius:3.0 module is now available for Red Hat Enterprise Linux 8.8 Extended Update Support.
Read more... -
Red Hat Security Advisory 2024-4830-03
Operating System: RedHat ≈ Packet Storm Jul 25, 2024 | 13:15 pmRed Hat Security Advisory 2024-4830-03 - An update for the httpd:2.4 module is now available for Red Hat Enterprise Linux 8.4 Advanced Mission Critical Update Support, Red Hat Enterprise Linux 8.4 Update Services for SAP Solutions, and Red Hat Enterprise[…]
Read more... -
Red Hat Security Advisory 2024-4831-03
Operating System: RedHat ≈ Packet Storm Jul 25, 2024 | 13:15 pmRed Hat Security Advisory 2024-4831-03 - An update for kernel-rt is now available for Red Hat Enterprise Linux 9.2 Extended Update Support.
Read more... -
Red Hat Security Advisory 2024-4836-03
Operating System: RedHat ≈ Packet Storm Jul 25, 2024 | 13:15 pmRed Hat Security Advisory 2024-4836-03 - Updated images are now available for Red Hat Advanced Cluster Security. The updated image includes new features, bug fixes, and updates to patch vulnerabilities.
Read more... -
Red Hat Security Advisory 2024-4823-03
Operating System: RedHat ≈ Packet Storm Jul 25, 2024 | 13:14 pmRed Hat Security Advisory 2024-4823-03 - An update for kernel is now available for Red Hat Enterprise Linux 9.2 Extended Update Support. Issues addressed include denial of service, double free, and information leakage vulnerabilities.
Read more... -
Red Hat Security Advisory 2024-4824-03
Operating System: RedHat ≈ Packet Storm Jul 25, 2024 | 13:14 pmRed Hat Security Advisory 2024-4824-03 - An update for the nodejs:18 module is now available for Red Hat Enterprise Linux 8.8 Extended Update Support. Issues addressed include a denial of service vulnerability.
Read more... -
Red Hat Security Advisory 2024-4825-03
Operating System: RedHat ≈ Packet Storm Jul 25, 2024 | 13:14 pmRed Hat Security Advisory 2024-4825-03 - An update for podman is now available for Red Hat Enterprise Linux 9.0 Update Services for SAP Solutions. Issues addressed include deserialization and memory exhaustion vulnerabilities.
Read more... -
Red Hat Security Advisory 2024-4826-03
Operating System: RedHat ≈ Packet Storm Jul 25, 2024 | 13:14 pmRed Hat Security Advisory 2024-4826-03 - An update for the freeradius:3.0 module is now available for Red Hat Enterprise Linux 8.6 Advanced Mission Critical Update Support, Red Hat Enterprise Linux 8.6 Update Services for SAP Solutions, and Red Hat Enterprise[…]
Read more... -
The Product Security Blog has moved!
Red Hat Security Blog Blog Posts Mar 19, 2019 | 19:38 pmRed Hat Product Security has joined forces with other security teams inside Red Hat to publish our content in a common venue using the Security channel of the Red Hat Blog.This move provides a wider variety of important Security topics,[…]
Read more... -
New Red Hat Product Security OpenPGP key
Red Hat Security Blog Blog Posts Aug 22, 2018 | 13:30 pmRed Hat Product Security has transitioned from using its old 1024-bit DSA OpenPGP key to a new 4096-bit RSA OpenPGP key.This was done to improve the long-term security of our communications with our customers and also to meet current key[…]
Read more... -
SPECTRE Variant 1 scanning tool
Red Hat Security Blog Blog Posts Jul 18, 2018 | 13:30 pmAs part of Red Hat's commitment to product security we have developed a tool internally that can be used to scan for variant 1 SPECTRE vulnerabilities. As part of our commitment to the wider user community, we are introducing this[…]
Read more... -
Red Hat’s disclosure process
Red Hat Security Blog Blog Posts Jul 10, 2018 | 13:00 pmLast week, a vulnerability (CVE-2018-10892) that affected CRI-O, Buildah, Podman, and Docker was made public before some affected upstream projects were notified. We regret that this was not handled in a way that lives up to our own standards around[…]
Read more... -
Join us in San Francisco at the 2018 Red Hat Summit
Red Hat Security Blog Blog Posts Apr 23, 2018 | 14:30 pmThis year’s Red Hat Summit will be held on May 8-10 in beautiful San Francisco, USA.Product Security will be joining many Red Hat security experts in presenting and assisting subscribers and partners at the show.Here is a sneak peek at[…]
Read more... -
Certificate Transparency and HTTPS
Red Hat Security Blog Blog Posts Apr 17, 2018 | 15:00 pmGoogle has announced that on April 30, 2018, Chrome will:“...require that all TLS server certificates issued after 30 April, 2018 be compliant with the Chromium CT Policy. After this date, when Chrome connects to a site serving a publicly-trusted certificate[…]
Read more... -
Let's talk about PCI-DSS
Red Hat Security Blog Blog Posts Feb 28, 2018 | 14:30 pmFor those who aren’t familiar with Payment Card Industry Data Security Standard (PCI-DSS), it is the standard that is intended to protect our credit card data as it flows between systems and is stored in company databases.PCI-DSS requires that all[…]
Read more... -
Security is from Mars, Developers are from Venus…...or ARE they?
Red Hat Security Blog Blog Posts Nov 16, 2017 | 15:00 pmIt is a tale as old as time.Developers and security personnel view each other withsuspicion.The perception is that a vast gulf of understanding and ability lies between the two camps.“They can’t possibly understand what it is to do my job!”[…]
Read more... -
Abuse of RESTEasy Default Providers in JBoss EAP
Red Hat Security Blog Blog Posts Oct 18, 2017 | 13:30 pmRed Hat JBoss Enterprise Application Platform (EAP) is a commonly used host for Restful webservices. A powerful but potentially dangerous feature of Restful webservices on JBoss EAP is the ability to accept any media type. If not configured to accept[…]
Read more... -
Kernel Stack Protector and BlueBorne
Red Hat Security Blog Blog Posts Sep 12, 2017 | 11:51 amToday, a security issue called BlueBorne was disclosed, a vulnerability that could be used to attack sensitive systems via the Bluetooth protocol. Specifically, BlueBorne is a flaw where a remote (but physically quite close) attacker could get root on a[…]
Read more...
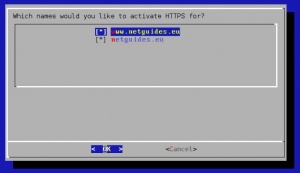
Let’s Encrypt empfiehlt einige Clients, die mit CentOS kompatibel sind. Wir denken, dass CertBot von der non-profit Electronic Frontier Foundation eine sehr gute Wahl ist, wenn dieser richtig eingerichtet ist und beschreiben daher diesen.